"Talos: Encrypted Query Processing for the Internet of Things", Hossein Shafagh, Anwar Hithnawi, Andreas Droescher, Simon Duquennoy and Wen Hu. The 13th ACM Conference on Embedded Networked Sensor Systems (SenSys 2015), November 2015, Seoul, South Korea. In-press.
Abstract: The Internet of Things, by digitizing the physical world, is envisioned to enable novel interaction paradigms with our surroundings. This creates new threats and leads to unprecedented security and privacy concerns. To tackle these concerns, we introduce Talos, a system that stores IoT data securely in a Cloud database while still allowing query processing over the encrypted data. We enable this by encrypting
IoT data with a set of cryptographic schemes such as order preserving and partially homomorphic encryptions. To achieve this in constrained devices, Talos relies on optimized algorithms that accelerate partial homomorphic and order preserving encryptions by 1 to 2 orders of magnitude. We assess the feasibility of Talos on low-power devices with and without cryptographic accelerators and quantify its overhead in terms of energy, computation, and latency. With a thorough evaluation of our prototype implementation, we show that Talos is a practical system that can provide a high level of security with a reasonable overhead. We envision Talos as an enabler of secure IoT applications.
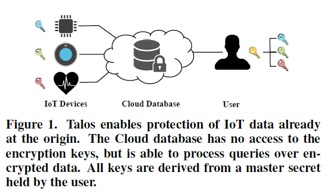
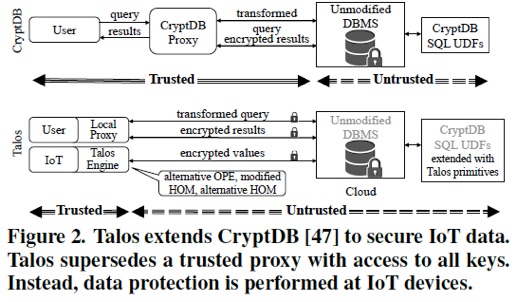
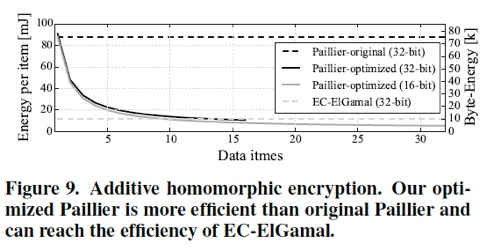
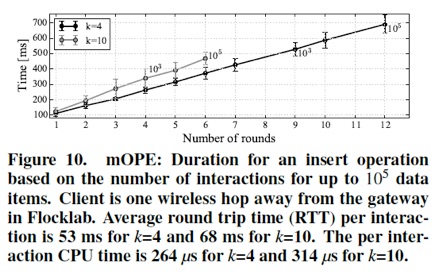
Case Study. Let us again consider the application scenario of the health monitoring device which logs heart rate, location, and timestamps. The logged information have different sensitivities. For instance, the heart rate measurements have the highest sensitivity, since they can be used to infer health-related information about a person (e.g., stress, depression, or diseases). Hence, Talos protects heart rate with additive homomorphic encryption to provide semantic security and allow average and summation computations. Health monitoring devices typically sample at 1 Hz (every 1 s) during sport activities and 6 times per hour otherwise. For a person with 1 h sport activity per day, this would result into a daily 3,738 data items encrypted with additive homomorphic encryption. The location, logged every 15 min, is maybe less sensitive for this person and could be encrypted with deterministic encryption, to allow encrypted queries correlating heart rate with location. Hereby, the timestamp for each heart rate record could be encrypted with order preserving encryption, to allow ordering, but not reveal the actual time.
Assuming the same underlying platform we used in our evaluation, the total daily energy cost of additive homomorphic, deterministic and oder preserving encryptions in this scenario accounts to a total of 42.67 J per day. This would contribute to a modest 5.4% of the daily energy budget of a Fitbit with 5 days lifetime and a lithium-polymer battery capacity of 1.2 Wh (4.32 kJ)




