School of History, Philosophy and Politics
Macquarie University, Sydney
School of Computer Science and Engineering
The University of New South Wales, Sydney
avincent@laurel.ocs.mq.edu.au
jas@cse.unsw.edu.au
http://www.ocs.mq.edu.au/~avincent/
http://www.cse.unsw.edu.au/~jas/
Abstract: In this article we describe how the Internet and the World Wide Web have been used to add a new dimension to the teaching of Middle East Politics. Students carry out extended role-play simulations, via the mechanisms of e-mail and chat-rooms, to conduct Middle East diplomacy. In the process, they learn about both the specifics of Middle East politics and international relations in general. Student evaluation of the simulation has indicated that they provide an effective learning environment, providing both motivation to study and "hands-on experience" in the practice of international relations.
Keywords: role-play simulation, Middle East politics, international relations, electronic mail, Internet, World Wide Web
Interactive Demonstration: the Chat-room (referenced in several places) requires a browser that can handle JavaScript, as does the new Web-based interface.
Such actions are seen by Australian students on television, but are often not fully understood, either by the students or by the television presenters themselves. In other words, while the Middle East is very topical, it is also confusing and bewildering. Making sense out of this constantly changing kaleidescope poses a challenge to student and teacher alike.
In recent years the politics of the Middle East have been taught to undergraduate students at Macquarie University through the use of Internet-based role-play simulations played out with politics classes at other universities. These role-play simulations are conducted as an integral, and assessed, component of Middle East Politics subjects at Macquarie, and replace the exam in the subject.
The aim of the simulations is threefold:
This article describes our experiences in developing and implementing role-play simulations with the aim of providing an overview of our methods and a discussion of their pitfalls and achievements to other teachers who might consider using role-play simulation via the Internet in their own subjects. While we naturally focus on the details of our Middle East politics simulation, many of our observations would apply equally to Internet-based role-play in other disciplines such as history, law and industrial relations, as well as to politics and international relations more generally.
In this article, we give the educational and technological background to the simulations, describe how they work, give a history of their development, discuss their effectiveness, and suggest future directions for improvement. Note that we use the term simulation throughout this article as an abbreviation for Internet-based role-play simulation.
Neo-Vygotskians (such as (Driscoll,1994)) suggest that effective learning takes place when teachers challenge students with problems that are beyond their existing level of experience and facilitate the process of finding the solution to such problems. The Simulations certainly introduce students to problems (in international diplomacy) that are outside their current realm of experience, and the presence of the Controllers and the academic staff, as well as interaction with other students, provides the necessary guidance in developing strategies for solving these problems.
Gredler (1992) identifies two major classes of simulations: tactical-decision simulations and social-process simulations. In tactical-decision simulations, the emphasis is on the collection and interpretation of data and the development of a strategy to achieve a specific goal. In social-process simulations, the emphasis is on the study of human interactions and communication in pursuing social or political goals. In Gredler's (1992) taxonomy, our political science simulations fall into the category of multi-agenda social-process simulations. In such simulations, "participants assume individual roles in a hypothesised social group and experience the complexity of establishing and implementing particular goals within the fabric established by the system".
Simulations have a number of advantages as a learning method where the aim is to gain an appreciation of processes or complex dynamic social systems. Almost all studies on simulations have highlighted their motivational capacity and their ability to provide students with direct experience of complex systems. For example, Maidment (1973) notes that "simulation techniques heightened motivation and experience and that students gained a greater appreciation of the complexities of the international system". Brookfield (1990) suggests that the motivational aspect is related to students coming to "regard learning activities as having immediate relevance" and that this leads to "learning to be recalled long after it has happened". Brookfield also notes that simulations involving international relations cause the students to be "made more aware of their own assumptions, since they have to respond to others requests for explanations and justifications".
Some advocates of experiential learning take the even stronger view that learning methods such as simulations are the most potent form of learning. Kolb (1984, p.38) states that "learning is the process whereby knowledge is created through the transformation of experience". In this view, learning cannot occur without some kind of "transaction between the learner and the environment". In the case of learning about complex social systems, the only possible way to gain such experience from outside such a system is via simulation.
While simulations and role-plays motivate students to become intensely involved, there is also a danger that the students may lose sight of the educational objectives. Brookfield (1990) notes that, in classroom-based simulations, "because of the emotionally-charged nature of simulations and role-plays, students need to feel that they are not being taken advantage of or made to look foolish for no good educational reason". Jaques (1992) puts a slightly different perspective on this in noting that the students who get most out of simulations "are those who are able to maintain a delicate balance between play and reality".
Simulations and role-plays are demanding not only on the students, but also on the teacher. Brookfield (1990) notes that considerable effort is required in setting up a simulation scenario, ensuring that students are briefed on their roles, and in de-briefing them afterwards to ensure that they take the intended points away from the simulation experience. This last point is particularly important, since simulations require the teacher to relinquish control of the learning environment, and thus allow the process to move in possibly unexpected directions. Brookfield (1990) mentions this as another reason why simulations are demanding on teachers; they require that teachers, who are used to being in control of the learning environment, step back and "let things run". Teachers also need to be ready to handle unexpected situations that may arise during the course of a simulation.
Person-to-person interactive dialogue is used for one-on-one discussions, which in real life might be conducted either via the telephone or via a private meeting (most likely with a small group of advisors). Small group dialogue is used for small meetings which might be conducted either in person or, increasingly, via a teleconference. Communiques are used to convey information in written form either between individuals or among small groups, and would typically be used to formally state support, issue diplomatic protests, and so on.
Nowadays, the media plays an important role as a channel of communication between political leaders and the public. While "the public" are not directly modelled in these role-play simulations, the media is important as a vehicle for shaping perceptions of the various characters among other players who may not be in direct contact with them. In the context of the simulations, publication facilities outside the media are required to make the role profiles (details of each participating character) available to all players.
The Internet already provides facilities for all of these kinds of communication (e-mail for communiques, "chat rooms" for interactive dialogue, Usenet news or the World Wide Web for media and publication). In all of the simulations up to 1998, we made use of simple existing Unix-based tools for each of these communication media. E-mail was handled using the elm mail client along with a set of aliases for individuals and small groups. Interactive dialogue was handled via the talk program, with a shell wrapper to provide role-name access to other players. The talk system supports only one-to-one dialogue, and so, where available, we also made use of the ytalk program which supports multi-user dialogue. The media was also handled via e-mail, using mail aliases. Publication of role-profiles was, up to 1995, via paper; since 1996, we have placed role-profiles on the Web. In 1997, we experimented with a simple Web-based "chat" system. We are presently (1998) implementing an integrated Web-based system which handles all of the communication needs of the simulation.
An important feature of using the Internet is that it allows students in several different countries to participate in each role-play simulation. However, this also creates problems in dealing with time-zone differences and network availability. Thus, we have also provided facilities to allow students to check availability of other network sites and players. This was achieved by making use of the Unix finger tool for querying site/user status, and supplying a wrapper that translated login-names to role-names.
One of the first significant long-term uses of simulations in higher education was by Interactive Communications and Simulations (ICS) group at the University of Michigan (Taylor et al. (1987)). Beginning with classroom-based simulations in 1973, they ran the Political Science 353 subject as a series of simulations, each of which approached "the subject of Arab-Israeli Affairs from a different perspective". In 1983, they moved the simulations to the computer-based CONFER system hosted on Michigan's main computer system. Nowadays, the ICS group (1997) provides a number of simulations in various areas of study.
The Arab-Israeli simulations are conducted via a system of conferences (essentially e-mail groups) among members of one class. Roles are allocated to individual students, and the simulation proceeds over 11 weeks (five weeks preparation, four weeks simulation, two weeks de-briefing). Roles are grouped into teams by national or ideological interests. Discussion is carried out primarily by email in this system.
Another educational simulation group, Project ICONS (1997), developed in the 1980s at the University of Maryland. From its inception, Project ICONS used computer-based simulations, generally on politics and international relations themes. Its initial interface was a simple text-based system, POLNET, similar to the CONFER system used by ICS, but Project ICONS has recently developed a Web-based interface (ICONSNET). Project ICONS now runs computer-based simulations commercially for high-schools and universities, generally on politics and international relations themes. Project ICONS provides a similar set of facilities to our new Web-based simulation software, including mail, conferencing (although the interface is less immediately interactive than talk or our Web-based chat).
When Andrew Vincent began teaching Political Science in Australia in 1989, he wanted to incorporate some kind of role-playing exercise into his teaching to invigorate the learning of Middle East Politics. He had come in contact with role-play in the United States, where simulations had been played by a single class "in-house" over a short period such as a day or a weekend, using runners to carry messages between the players. In co-operation with John Shepherd, a computer scientist and the co-author of this article, he devised a way of using the Internet to conduct simulations not just within a single class but with politics classes in overseas universities, using electronic mail, the Internet and the World Wide Web.
This has proved to be much more effective than in-house simulations as it adds an unknown and exotic dimension for the students; they are not just playing against their class-mates, but against students in another country and with a substantially different world-view. At the same time it goes some way towards countering Australia's geographical isolation by bringing the students more in touch with the wider world. The technique also introduces Arts students to more esoteric aspects of computing than they would normally be expected to know.
So far, thirteen simulations have been completed, involving the following Universities:
These simulations have received considerable local publicity in Australia (Alexander,1996; Back,1996; IDP,1995; Latona,1996) and have even attracted attention in the United States (Chronicle,1992; Hudson,1993; LaQuey,1993). In 1995 they were selected by IDP Education Australia for showcasing to the OECD as one of the four best examples of internationalisation of education in Australia (IDP,1995). Through them, not only Macquarie University but Australia itself has gained a steadily growing reputation for technology-aided teaching.
Several of the real-life characters that the students "play" have also heard about them, such as Hannan Ashrawi, the late Yitzhak Rabin, Yasser Arafat, and King Hussein of Jordan. So too, have most of the Middle Eastern Embassies in Australia and the Australian government's Department of Foreign Affairs and Trade. It is also not unreasonable to speculate that various intelligence organisations are aware of the simulations, since simulation messages regularly contain words (such as "terrorist", "Palestinian", "Libyan" etc.) that these organisations routinely search for in electronic mail traffic.
Almost from the beginning the US Consulate heard how the simulations linked Australian students with their counterparts in the US, and offered facilities for two to three hour teleconferences. These teleconferences enable each simulation to be concluded with a real-time conference, where students are linked by speaker phone to their colleagues in the US and other countries and can actually talk to the people they have been writing to.
After the roles have been determined, the students form teams of three or four, and teams are allocated roles; that is, they are given the task of playing out the role of a prominent political, religious or social leader in the Middle East, Europe or the United States, such as King Hussein of Jordan, Yasser Arafat, or Bill Clinton. Each team is also assigned a computer account. Thus far, teams have always been based at a single university. This is probably the best arrangement in any case, since teams need to spend a considerable amount of time discussing their actions, something that is much easier to achieve if the team members can physically meet or telephone each other on a daily basis.
The distribution of roles between participating universities has varied from simulation to simulation. On some occasions, for example, we have insisted that American students play American roles; on other occasions, we have given the American roles to non-American students. Both approaches seem to produce effective results, and either approach can lead to some interesting self-appraisal by the students (for example, American students being shocked at how non-Americans play American roles).
Once teams are formed, the first task for each team is to develop a role profile: a description of the political agenda, character traits, background, interests, long- and short-term political objectives, and potential allies and opponents of the character they are playing. This is a very important task, and requires the students to engage in a considerable amount of research. Our experience has been that students show considerable initiative in tackling this task. For example, many have contacted the embassy of their role character, and this has often been their first contact with politics outside their domestic political scene. For many, also, it is their first attempt at "real" research.
With the introduction of the World Wide Web into the Simulations, we have also begun encouraging the students to use the Web for research. To assist with this, we have set up a Middle East Links page under the Simulation Web page. The questionnaires from the most recent simulations show that the majority of students now conduct their role profile research via the Web, with support from the University library.
Role profiles are then made available to all the participating students through the World Wide Web. This is actually useful from two perspectives. First, it makes all of the biographical information about the roles available to everyone, which encourages more accurate simulations. Secondly, because students know that their work will be available for everyone to read, they take more pride in it than they might in an essay destined for the desk of an anonymous marker. The fact that role profiles are now available via the Web also encourages students to be creative in their production.
Around one week before the simulation actually starts, the students are given a practice session on using the computer system. This session lasts for around two hours, and they can then practice using the system until the simulation proper begins. The level of computer literacy varies considerably over the student population, but most teams usually contain at least one person who has some computer background or "catches on" quickly and can help the others to become familiar with the system. In order to assist players with the computer system, a considerable amount of help information is contained in the simulation Web pages. There is also a set of simulation guidelines to suggest more general strategies for effective role-play.
Finally, students are given the home phone numbers of all the other players, so that they can have an avenue to plan strategy outside the computer system. Every simulation generates at least a few international phone calls, as well as many local calls.
The students then respond to these events by communicating with each other using electronic mail and on-line "chat" systems or even telephone to develop the political situation to their advantage. The aim of each group is to advance their character's interests as far as they can, keeping within the parameters of reality, and the role profile.
As in real life, various communication modes are available. Players can communicate with: other individual players to simulate private discussions and diplomatic communiques; with small groups of other players for regional conferences and meetings, with all other players to simulate press releases.
As well as political roles, the simulations also contain media roles, such as the BBC World Service, CNN, or the New York Times (there is usually one media role for each participating university). As in real life, the media is responsible for keeping all the players up to date with latest developments, through the simulation pages on the Web. Media players can indulge in investigative journalism, interview other players, and sometimes even receive "leaks" from the simulation controllers.
All communication is monitored by game controllers (see section 4.6) at each participating institution, in order to prevent excesses, resolve disputes and grade the performances. If players wish to undertake violent actions against other players, they must first submit their plans to the scrutiny of all of the controllers. The controllers determine the plausibility of the action and either allow or disallow it. If the controllers cannot agree on the "legality" of an action, it is referred to the lecturers, who have, thus far, always managed to resolve the question amicably.
Students are free to say whatever they like in their messages, but there are certain ground rules which all teams must observe. For example, players cannot kill each other, and major actions/initiatives need prior approval from the controllers. Actions without such approval can be disallowed, and the team's grade will suffer accordingly. But essentially, the students play their roles themselves, without outside assistance. We have found that the teams tend to be largely self correcting, through the other team members, and the other players in the game.
The teams play outside scheduled class time, from terminals at the university or from personal computers at home via modem. The average simulation lasts for about three weeks, during which time each team receives on average 10-20 messages per day and produces on average 3-10 messages per day (50-200 messages over the course of the entire simulation). In order to handle this amount of email traffic, as well as monitor the media reports, and conduct talk discussions, teams often spend four to five hours per day at their computer terminals. In order to reduce the amount of time individuals spend on-line, teams often work in shifts, although they meet frequently to discuss strategy. We have even found that the time-zone difference between Australia and the USA does not cause major problems, because students on both sides of the Pacific are willing to work through the night at the height of the simulation.
During the course of a normal simulation, thousands of electronic mail messages are generated, and it is these that are graded. Transcripts of all messages are kept by simulation controllers for assessment. The messages from the best students often reveal a combination of careful research and fertile imagination, for there is enough scope in the simulation for imagination and initiative to have a lasting impact.
While international telephone link-ups were not available for the first few simulations, teleconferences are now an important part of each simulation. The students know about them in advance, and plan their strategy in the three weeks of the game accordingly. They are entirely student-run, and the students themselves must jointly work out an agenda (the first 1997 agenda is a good example), an order of speakers and the time allocations for each speaker.
The teleconferences give students experience in mounting and participating in an international conference, with everything that that entails, such as nervousness, unpreparedness, misunderstandings and downright bullying. So far, the teleconferences have relied on audio links only, but in the future a video hook-up where the students can see as well as hear each other could be anticipated. In fact, at the recent teleconference (since May 1997), CU-SeeMe links were available for private negotiations.
Each student is also asked to fill out a questionnaire aimed at providing formative and summative feedback on the simulation method itself. This questionnaire aims to discover what students have gained from the experience, and to discover ways in which the simulations can be improved.
Teams are assessed on a number of measurable criteria, including: the role profile; the quantity of communications as measured by the computer system; the much more subjective quality of communications; performance in the teleconference; and the final simulation report. Each of these components attracts equal assessment weight. In some recent simulations, which have been run close to the end of semester to fit in with North American teaching time, we have not required a final report.
The simulation, like the exam which it replaces, is worth around 40% of the grade for the subject. The students are still required to write essays, tutorial papers and so on, so the more conventional methods of assessment are not entirely done away with. Similarly, the students are still expected to attend normal lectures and tutorials.
Controllers are typically drawn from the tutors in the subjects or are senior students who have previously undertaken simulations. They are required to monitor all mail in the simulation and tell students if a piece of mail is too far out of character or has moved outside the bounds of plausibility for the simulation. As well, students are told to confer with the controllers before undertaking any major actions against other players. Controllers will either disallow such actions or modify them to more accurately reflect a real-life outcome. They also have the option of leaking information to intelligence agencies or the news media.
In order to perform their task effectively, controllers must have a deep understanding of Middle East politics and international relations. However, if some question arises which they feel is beyond their means to answer, controllers also have the option of conferring with the lecturer. In a sense, controllers provide a buffer between the academic staff and the day-to-day running of the simulation. They also provide valuable feedback to the academic staff when they come to assess the quality of each team's contribution to the simulation.
In order to keep up with the progress of the simulation, a considerable time commitment is required from controllers (typically of the order of 3-4 hours per day). Controllers at Macquarie are paid for their efforts, although many would be willing to perform the task gratis in order to maintain their involvement with the simulations.
One simple piece of evidence that indicates effective learning is that students are required to write an essay near the start of semester (before the simulation) and another towards the end. The depth of understanding shown in these essays improves considerably after students have done the simulation. Whether this is due to the simulation or simply to learning during lectures, tutorials and reading is, however, open to debate, especially in the absence of controls who take the subject without doing the simulation (despite the simulation being optional, all students choose to participate).
In this section, we present an informal discussion of how students interact in the simulation and how they perceive the experience afterwards.
In this simulation, Rifaat al-Assad, the brother of Syrian president Hafez al-Assad, decided to assume control of Syria for several reasons. First, and possibly somewhat out of character, the role playing Hafiz al-Assad was being relatively inactive in the simulation, and Rifaat decided that Syria should have a larger involvement. Second, and more in character, he had grand plans to form a major alliance of strongly anti-Israel Arab leaders and use Syria as the launching pad for a major offensive against Israel. The following sequence of messages shows how he accomplished his aims by first securing alliances, confirming the coup with the simulation Controllers, managing international perception of the coup, and, ultimately, faltering under the counter-coup.
To: Bill Clinton
From: Rifaat al-Assad
Greetings friend. You nor I have never spoken before until now. I am
writing to you from my home in Pasadena where I have been vacationing
for a number of months now. I try to get to America as often as I can,
when i have the time that is.
I have some information for you Mr Clinton, It has come to my attention
through my various aides in and around the Gulf states that King Hussein
of Jordan has gained access to your secret files and messages...
In return for supplying this information. I ask a boon of you. The current
Syrian president Hafiz al Assad is gravely ill. He can no longer function
in any official capacity. During the time of his reign, relations between
Syria and the US have been strained, particularly during the cold war. As
for my part, I have constantly been referred to as a Saudi and an American
puppet, why not make the repartee official. I hereby ask of you to write
to the controllers of the sim pledging your support for my replacing my
ill-brother as president of Syria... Please write to Control and pledge
your support for my new (US friendly) regime.
To: Saddam Hussein
From: Rifaat al-Assad
Greetings brother. The time for the coup is at hand. Control will mail
you asking you whether or not you will support me in it, I'm sure that
you will, however. Our anti-western alliance (myself, you, Rafsanjani
and Gaddafi) has been cemented. All that needs to be done now is for me
to gain power...
To: Control
From: Saddam Hussein
Iraq has decided after many formal negotiations with Rifaat al-Assad
that we will support his move to overthrow his brother, and gain control
over the Syrian people. We believe this move to be in the best interests
of Syria and the Middle East as we see it.
To: Rifaat al-Assad
From: Mu'ammar Qaddafi
We write to you in the spirit of friendship and mutual support that our
two nations have enjoyed for some time now. Be Assured that the Libyan
Arab Jamahiriya wishes for this situation to continue and hope that the
Syrian government continues to involve Libya in diplomatic discussions
involving Israel, Palestine, the Kurds and Arab unity. Libya is in a
position to help you and hope that we can work together to drive out
the infidel Israelis and their imperialist Western allies.
To: Jacques Chirac
From: Rifaat al-Assad
Bonjour, Ca'va ?
Upon hearing of your support for my push I am driven to ask you if
there is anything I can do for yourself and your interests when I gain
power ... let me know If I can be of any assistance (i.e. contacts with
Gaddafi could ensure a substantial diversion in the actions of the GIA).
To: Bill Clinton, Madeleine Albright, CIA,
King Hussein, Sfeir, Netanyahu, Arafat, CNN
From: Chirac
French intelligence has for some time been aware of the likelihood of
a coup in Syria by Rifaat al-Assad. I am sure you have likewise been
appraised of the situation.
The French government feels it is now time to speak out and voice our
support for this move. The administration of Hafiz al-Assad has for some
time been a thorn in the side of the chance of a peaceful resolution to
the Arab-Israeli conflict, and I feel that Syria under this new regime
may be able to assist in our collective effort to end the terrorist
threat of the Hizbollah, and improve relations with Israel.
I call on all parties to support this coup and the revived spirit of a
peaceful resolution to our problem it brings.
To: Syrian Muslim Brotherhood
From: Rifaat al-Assad
(To make things official). I think we both know that it is in our best
interests to keep in friendly contact with each-other for the up-coming
mobilisation on the Israeli border.
My regime WILL NOT BE A MILITARY ONE. I have achieved executive power
through legal and peaceful means..
To: Maronite Patriarch Sfeir
From: Rifaat al-Assad
Greetings brother...
Firstly, your worries concerning Hizbollah. I may not have made my plans
clear in my last communication. When I said that I was to offer them
positions in my border guard, I mean to do so in such a way that I have
trusted officers keeping an eye on them, making sure they behave etc.
Concerning Hariri, I like your idea of a unity govt, to keep things
stable, both in Damascus and Beirut. An idea such as this would fit
perfectly into the framework of the Yeesevenbee (E7B) Alliance.
The Controllers permitted the coup to proceed, after warning Hafiz al-Assad that it was imminent and receiving no response. In the following example messages, Rifaat al-Assad reports the coup to the media and attempts to gain international support. The coup story was never reported by CNN, and so he had to use his own means of alerting potential allies.
To: CNN
From: Rifaat al-Assad
My forces have surrounded my brother's stronghold at Aleppo, sortie's
into the streets of the rural town are being conducted on the hour. We
expect to uncover my brother's hiding spot within a few hours.
It would also be helpful if you could declare the official existence
of the AFC- The Arabic Freedom Council. The council consists of: Syria,
Libya, Iran, Iraq - head of state involvement. On a smaller level, many
bureaucrats and academics are involved (Kaddoumi etc). If you chose not
to publicly broadcast our existence, then we'll do it ourselves, it is
of no matter..
To: CNN and many world leaders
From: Rifaat al-Assad
***COUP UPDATE***
Greetings and salutations to you all.
In mailing this communication I hereby declare myself to be the new
President of the Arab Republic of Syria (certified by control). Only
hours ago, my coalition forces of my own loyal defence companies and
the Syrian Muslim Brotherhood stormed the presidential compound in
Damascus. We encountered little resistance during this exercise. The
state of the presidential suite indicates a hurried and desperate retreat
on the part of my brother Hafiz, who at this stage has evaded capture.
Some might ask how did I overcome the might of his special forces
batallion surrounding the compound? This was done via the SyrianMB who
had been holding secret talks with the upper echelons of Hafiz's guard
for a number of weeks. Many of the guard, although of alowite origin
are believed to be discontent with the current regime and have taken on
Sunni sympathies.
The following message shows that some important interaction takes place off-line. The E7B mentioned in the message is a building at Macquarie University.
To: Controllers
From: Rifaat al-Assad
OK here's the deal:
In an attempt to compete with the already established power bloc
comprising the various Israeli factions, The Americans, Saudi's and
Jordanians, a secret gathering was held this morning in a small Syrian
town known as E7B. The parties taking part in the discussion included:
Iranian Prime Minister Heshemi Rafsanjani
Libyan leader Mu'ammar Qaddafi
Iraqi president Saddam Hussein
Yours truly Rifaat al Assad.
A very interesting group of people I'm sure you will agree. For the most
part, the meeting consisted of trying to convince Rafsanjani and Saddam
to sit in the same room together, but to no avail.
The four of us (and our various aligned terrorist groups - Hamas,
SyrianMB, Hizbollah) have decided to pool our resources together in
an effort to stave off what we believe to be an attempt to discredit
and disempower the Arabic peoples, recent American actions in Iran are
testimony to this. In practical terms our alliance consists mainly of:
1. Military support - in terms of arms and training. 2. Sharing of
Strategic knowledge (mabye not between Iran and Iraq) 3. A combined
unilateral anti-western, anti-Israeli doctrine.
In order for this alliance to come to it's full fruition, control must
soon acknowledge me as the new (or temporary) LEADER (not pres) of Syria..
On occasion, the intensity of the simulation can cause personal conflicts among the players, as the following example shows. In such cases, the Controllers have an extremely important role in calming the players.
To: Control1
From: Rifaat al-Assad
I know you said to write to "control" but this letter is a bit outside the
sim. It's something I'd prefer to talk to you in person about but you're
not online or around and it needs urgent attention.
It's pretty much become open knowledge that the Sim (OZ wise) is turning
into a personal vendetta, with the players playing Mossad, King Hussein,
Clinton, Netanyahu, etc. forming their own little scheming bloc with the aim
to wipe out myself and the girls playing Rafsanjani. Having been around
political circles in various incarnations I can understand these things and
know best how to deal with them, but I'm afraid that the lines between
character and player are becoming increasingly blurred, with the
aforementioned bloc playing as a group of buddies - wheeling and dealing on
a personal level, not on the level of their characters.
A few personal attacks have been launched at me personally (ie Anti-semite)
.... It is things like this where people get dangerously emotional.
Naturally Rifaat al-Assad has no love for Jews/Israeli's so I portray that
in my character. I take grave offence however at the notion, that I (Mat) am
anti-semitic. Certainly I am very pro-palestianian and anti-zionist - but by
no means can I be likened to a David Irving..
Possibly somewhat out of character, the Israeli Prime Minister expressed support for Rifaat's coup. This naturally caused some consternation among his Rifaat's allies. This example shows the political "footwork" required to placate them. The reference to the University Bar indicates that some off-line discussions also took place on this matter.
To: Saddam Hussein
From: Rifaat al-Assad
Greetings brother and thank you for your support and congratulations.
I encourage you to rest assured about my stance on the Israelis. Their
willingness to co-operate with me is something of a mystery. I was
approached by one of Netenyahu's aides whilst working in Muhammeds Uni
Bar and was told by him that at the Amman conference, they all decided to
support me on the recommendation of Chirac. Chirac is one of my strongest
supporters so I assume he convinced them that I'm a workable personage.
Beliefs like this shall only aid us in the coming conflict. No-one will
expect the initial assault to some from Damascus, will they...?
The above examples show that students think about their responses to simulation events, and, while the language they use is no necessarily always in character, their manoeuverings are well-considered and demonstrate a reasonably mature attitude to diplomacy.
Some communication is out of character, but nevertheless provides an extremely useful contribution to the learning environment. The following demonstrates how students offer support to each other:
To: King Fahd
From: CIA
I understand your frustration 100%. You're doing a great job in your
role, and it's quite frustrating to see other people not to.
Re: Syria. the coup did not start out as a bad idea at all. When Assad
was sick in the past, one of his brothers did try to overthrow his
regime. They had missiles stationed around Damascus, and the whole bit.
Assad, however, was able to regroup.
In the sim, Rifat didn't do a very realistic "coup," and the
"counter-coup" by Hafez leaves serious questions behind. However, you
must keep in mind, that we're doing an exercise here. Although it's
frustrating, you must continue doing your best. Withdrawing from the
Conference is NOT an option. Believe me.
I played a role 2 years ago, if possible, w/ even more intensity as you
play yours. I was doing the sim 8 hours/day, and at a couple of points
I cracked; i couldn't take it. You manage to control yourself, and I
think it's very respectable.
I can give you only one piece of advice. Please, take it easy, don't
anger yourself unnecessarily. Write down the position King Fahd would
take in your place, and that's it. OK? Mail me if you need further
assistance.
Responses to the end-of-simulation questionnaires have been overwhelmingly positive, as indicated by the following examples:
I finally "saw the light" with regard to diplomacy, after two years studying Politics. The labyrinthine process finally became understandable...
An essay doesn't change whereas the questions we needed to answer fluctuated daily.
The questionnaires elicited responses from the students on five distinct aspects of the simulations: realism, educational value, technical issues, teleconference, and general impressions.
The first section of the questionnaire deals with how accurate a portrayal of the modern Middle East emerged from the simulation. The responses to these questions revealed that while some students had reservations about the accuracy, a significant majority felt that a realistic representation of the Middle East emerged.
Another focus of the questionnaires was on the usefulness of the simulation technique as an educational tool. Responses to these questions were overwhelmingly positive, although many of the students felt that the simulation was too time-consuming. With some exceptions, the experience of working in a team was a positive one, and the students' understanding of Middle East politics and international relations was enhanced. This bears out the claim of Jaques (1992) that "simulations ... give encouragement and credit to students finding, creating and using their own experiences and interpretations and sharing these with others through the interplay of the exercise".
The next section of the questionnaire addressed technical issues, and here the students' responses were much more varied, revealing a wide range of expertise in using computer technology. Some responses revealed a wide-eyed amazement at the communication potential of computers. Other students, with more computing experience, made specific suggestions to improve the computer system, such as being able to use the mail-reader of their choice, rather than the prescribed elm mail-reader. This wide disparity of experience is revealed starkly in the question related to the usefulness of the introductory computer tutorials; some students indicated that they learned almost nothing from the tutorials while others said that the tutorials assumed too much computer background.
The questionnaire then moved on to assess the contribution of the overseas universities and the significance of the teleconference. Here, the students' sense of fun became apparent, with comments about dressing up for the teleconference (in keeping weith Jaques' (1992) suggestion that simulations "reactivate the sense of fun and play associated with many of the most vivid experiences of childhood"). There were criticisms of the teleconference, but on the whole it seems to have been a positive and enjoyable experience for the students which served as a culmination to the simulation.
The last section of the questionnaire is more reflective, and asks the students their impressions of the best and worst features of the simulation, together with their suggestions for improvement. Responses to these questions, were detailed and informative, and revealed an appreciation of the educational experience of the simulation.
On the basis of these questionnaires, we have altered the ground rules of the simulations, and changed some of the technical aspects, making the system ever more user-friendly. The questionnaires have not only demonstrated the popularity of the simulations, but have also revealed the extra-curricular benefits the students have derived from them, such as the enjoyment of working in a team over a sustained period and of getting to know other people in the class. Indeed, the simulations seem to engender a spirit of camaraderie in Middle East Politics courses that is absent from most other Arts courses at Macquarie. The students also benefit by becoming more familiar with computers and the "information superhighway", knowledge which is increasingly essential in this day and age.
In short, the simulations are an intense learning experience, but at the same time, they are great fun. Students are agreed that they involve much more work than preparing for an exam, but the work is much more enjoyable. In the words of one of the students:
It made it easy to approach strangers in the class and have something common to talk (about).
It made the group closer, more friendly - a great change for such an isolating experience as an Arts degree.
As noted above, there are essentially five kinds of communication required by simulation participants:
While the simulation requires primarily communication facilities, because it is running over a network, it also requires status facilities to determine whether remote machines are running and who is currently logged in and active.
The technology developed for the simulations was influenced primarily by John Shepherd's experience with the Unix operating system, and by constraints on the amount of time available for software development. Once the decision was made to settle on the Unix platform, development of the system was largely a matter of choosing the most appropriate Unix tool for each of the above tasks and customising that tool to make it simpler to learn and use.
The major difficulties that we saw students facing were: the use of an editor to create email messages, and relating role names to "raw" e-mail addresses. For the first problem, we assumed that students would not require any sophisticated word-processing capabilities and that, in any case, many of them would already have rudimentary word-processing skills. Solving the second problem ultimately required the software to perform the mapping from role names to account names automatically.
An additional constraint on the simulation software was that it had to run on very simple computer systems. Many students play the simulation from home via a modem, and, until recently, most students accessed the university machines via a simple 24x80 vt100-style window. Thus, we make no assumptions about the availability of sophisticated workstations and graphics capabilities. This constraint is, nowadays, being relaxed somewhat with the growth in easy-to-use access to the Internet via the Web.

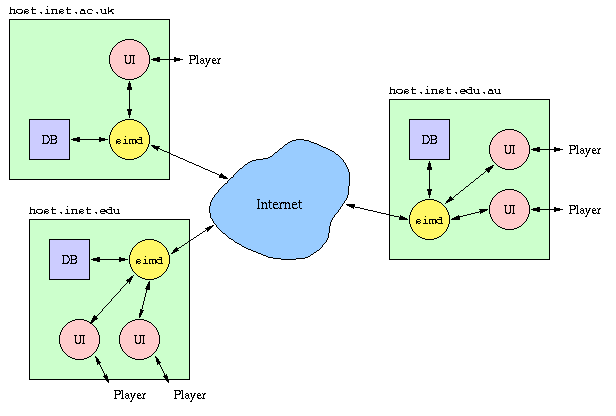
In the above diagram, the UI component represents the user interface to the simulation system, DB represents a database of all messages passed between players during the course of the simulation, and simd represents a "simulation daemon" that manages the interaction between the user interface, the database and the network.
In the second simulation, we were able to move to a Unix platform and use the elm e-mail system for asynchronous communication. We chose elm because it had a reasonably friendly user-interface and was highly configurable. The main configuration we performed was to install a list of "aliases" which allowed automatic routing of e-mail messages. Students could thus send mail to "Arafat" and it would be delivered to the appropriate team account, without the students needing to know any details of the real e-mail address. We also set up other aliases, such as "Arabs", that allowed mail to be sent to a group of users. As a side-effect of using aliases for mapping role-names to e-mail addresses, we were able to re-direct each piece of mail to the controllers' accounts, as well as sending it to the intended recipient.
For synchronous communication, we used the Unix talk command. This allowed two individuals to communicate, but did not have the capability for multiple users to conduct a discussion (on some of the systems we used, a multi-user version of talk called ytalk was available). The use of talk was simplified by the addition of front-end that allowed players to refer to other players via their role names rather than their account names. For status information, the Unix finger command proved to be adequate, once we placed a wrapper around it to convert account names into role names.
There were several problems identified with the system during this simulation. First, there were aliases such as "World" that allowed students to broadcast (mis)information to all players without any control. In subsequent simulations, this capability was restricted to the media roles. The second problem was the choice of editor. A large part of a student's time in the simulation is spent creating mail messages, and so it is important to have an easy-to-use editor for this task. Unfortunately, in this simulation, we made use of the default Unix editor vi, which is renowned as being difficult for novice users. In subsequent simulations, we switched to the joe editor, whose interface was more like the typical word-processing systems that students were likely to be familiar with.
In terms of our system architecture, UI was provided by a number of separate Unix commands, DB was the collection of mail in an individual user's account, and simd was comprised of the mechanisms that mapped role names to accounts.
The present system is made up of the following components:
Setting the configuration parameters was a one-time task that took less than one hour. Creating the alias file, once the academics have decided on a list of roles, requires less than two hours work, so there is not great on-going costs in setting up simulations.
The shell-wrapper required very little effort to produce, and the on-going costs are minimal since it uses an alias list that is produced from the elm aliases via a Perl script.
This script required somewhat more effort than the talkto script, since it has to cope with a range of network errors, but has the same minimal on-going costs as talkto since it uses the same alias list.
This is a very simple script, and also uses the same alias list as talkto and whoson.
The first problem was the way the talk command worked. In order to inform a player that someone else wishes to interact with them, the talk program writes a message on the screen on top of whatever work is currently being performed. This confused many of the students, who thought that their message had been destroyed, and were not sure how to respond in any case. Under Unix, what is required is that the user suspends the mail process temporarily, performs the talk and then resumes the mail process. These ideas made it considerably harder for the students to master the system.
The second problem was that there was no way to obtain transcripts of talk sessions, and so any interesting diplomacy that occurred in them would not be considered for grading. Since students make heavy use of talk to negotiate initial positions, this was a significant loss.
The final problem was the amount of e-mail traffic being generated. This was primarily as a result of the method used to deliver mail to the controllers. Every message was sent to not only the intended recipient, but also to every controller. A related problem was the amount of mail arriving in each team's mailbox. This quickly reached hundreds of messages, thus making the task of locating important old messages difficult. The elm mail system does have facilities for managing large amounts of mail (via the use of folders), but this also increases the difficulty of learning the system.
If network-based simulations are to be applied to other areas of teaching by other academics, the administration of the simulations needs to be made substantially easier. So far, setting up the software for each simulation has relied on the assistance of systems support staff from the Computing Services sections of the universities involved. In particular, they need to create a large number of accounts, set up the mail aliases, and install the wrappers which enable role names to be used. While this is not time-consuming (at most one or two hours work), it would be more convenient if the academic staff themselves could configure the system. So far, we have been very fortunate in having willing and able systems support staff (e.g. (Farquhar,1991)) in each University, who have assisted the simulations largely in their own time.
The above problems cannot be resolved given the technology base (Unix tools) on which the system is built. We are thus investigating the use of modern computer-supported cooperative work systems as a base for developing the simulation system further.
Over the last several years, Web technology has also developed, and we are making use of it for appropriate aspects of the simulation, such as archiving role-profiles. As of 1998, Web technology now seems able to support the all of the functionality that we require, and we are currently implementing a Web-based system that integrates e-mail, chat, news and status-checking. This system is being trialled in October 1998 and ought to solve all of the outstanding problems mentioned earlier in this section. In the future, we also plan to add configuration facilities to this system so that academics can set-up and monitor the simulations via a simple forms-based interface.
The lessons learned in the simulations can be treated at two levels: what the students actually gained by participating in the simulation, and what the academics involved have learned about the pitfalls of running simulations and strategies for making them more effective.
From the evaluation questionnaires and from discussions with students, we have identified three major benefits:
Putting yourself in someone else's shoes - you may get the role of a particular character but you don't necessarily agree with them but you have to try to develop their mindset. It's interesting. Right in there at the moment we've got a girl with leanings towards the Palestinians playing Benjamin Netanyahu, so it's a complete turn-around for her. It's imperative to be able to see other points of view and realise that they're just as valuable as yours.
I don't think I will ever look at any political situation again and take it at face value. There's so much involved under the cover of what's happening and you read between the lines ... I mean, we all see the solutions and say 'Why don't they do this?' But when you're actually here and everyone's in character ... you see how difficult it is and how almost impossible to implement a seemingly easy solution ...
It no doubt has provided extra insight into the complexities, idiosynchrasies, manoeuvring, wheeling and dealing, lying and hypocrisy of ALL politics. The Middle East just has its own particular flavour.
As teachers, one of the main lessons we have learned from the simulations are that they are an incredibly powerful tool for motivating learning. Any technique that can encourage students to spend several hours each day performing active learning must be interesting. Of course, it does have its disadvantages, in that students may end up neglecting other studies to concentrate on this one. This has not been reported as a significant problem in any of the simulations so far, but some mechanism (e.g. restricting login times each day) may be necessary to regulate student activity if it does become too time-consuming.
Another important lesson is in the area of Control decision-making. While students generally stay in the character of their roles, the intense competitive nature of the simulation could lead to anarchy if player actions are not kept in check. Here, the role of the Controllers cannot be underestimated. It is exceedingly important that Controllers at the different Universities communicate and agree on any controversial decision, and that such decisions are communicated to the students promptly and with sound justification. The ideal group of controllers would have sound knowledge of Middle East Politics and agree on strategies for handling player queries before the simulation commences.
As noted above, we have learned many lessons on the technological side of the simulation. The major one of these is that the time-frame of the simulation (around three weeks) is too short to expect students to spend any significant time learning how to use the simulation system. Ideally, we could leverage existing student knowledge of information technology to reduce the time required to learn how to use the system. While this was difficult in the early simulations, the advent and wide-spread use of the World Wide Web means that we can safely assume that students are familiar with a common interface, the Web browser, and build on this to develop easier to use interfaces.
Still on the technological side of the simulations, the present reliance on computer personnel to set up the simulation system is rather frustrating. We have been lucky so far in having the services of competent technical staff who were willing to devote some of their time to satisfying our requests. Even with their help, there is still a non-trivial amount of work required to set up the administrative aspects of the simulation (allocating roles, setting up mail aliases, cleaning up accounts). A major aim of the new Web-based simulation system is to reduce the effort required in these tasks, and to minimise the need for involvement from computer personnel. Ideally, the academic in charge of the subject should be able to set up the entire system themselves in a couple of hours.
The Controllers are put under considerable pressure during simulations. They receive a large number (more than 100) email messages each day and need to read all of these to keep apprised of all of the developments in the simulation, in order to make appropriate decisions. While they could take steps, such as appointing someone each day to summarise the major simulation activity for everyone else, more technical assistance in helping them deal with the incoming messages, and communicate with other controllers is needed (and planned in the new Web-based simulation system).
Computer-based role-play simulations, such as those described in this article, need not be restricted to the politics of the modern Middle East. There are a variety of other courses (such as other Politics courses, History and Languages) which could employ the technique, and they may even have an applicability outside the university, for example to diplomatic trainees, Defence personnel, or even to the Intelligence community. As such, they could be a potential money-earner in these days of university funding cut-backs. In time, it is hoped that the simulation software reaches a level of maturity where it could be marketed to other universities and outside organisations as a self-contained package, allowing these other organisations to mount their own simulations without our assistance.
From the perspective of Political Science, it is an interesting question whether the simulations could develop a predictive capability. Such a predictive capability, of course, relies on the simulation being a faithful model of the Middle East, and at first glance, it might appear that the simulations are too simple a model. However, there have been several occasions in past simulations where the students have accurately predicted subsequent events in the Middle East.
For example, in the March 1993 simulation, Macquarie students developed a deal between Yasser Arafat and Yitzhak Rabin over Palestinian autonomy in the Gaza Strip, excluding the West Bank leaders, who were in Georgetown. At the time, this seemed a little far fetched, but the Oslo Accords which resulted in Israel/PLO Declaration of Principles six months later proved the students to have been correct. In another example, during the September 1990 simulation, groups playing the roles of Yitzhak Rabin, Hannan Ashrawi and the CIA became so frustrated with the actions of the fundamentalist Jewish leader Meir Kahane that they requested permission from the controllers to assassinate him. Permission was denied according to the simulation rules, but it was interesting that some months later the real Meir Kahane was assassinated. Also, during the September 1990 simulation, the team playing the Syrian President requested permission to use their air force to attack General Aoun in Lebanon; within months, the Syrian leadership had dislodged the real Aoun using their airforce. Of course, these isolated examples do not demonstrate a general predictive capability, but the simulations invariably play themselves out in a manner which is consistent with the prevailing politics of the Middle East.
Despite the effort involved in setting them up, the simulations have been a rewarding application of new technology to a very old learning method, and they have attracted a significant student following to Middle East Politics subjects. Indeed there are students who now enrol in Middle East subjects solely because of the simulations and the reputation they have gained. In fact, over the last three years, enrolments in simulation-based Middle East Politics subjects have increased by 41%, in a period when overall enrolments have been stagnant at best and generally decreasing.
The simulations have helped students to grasp not only the intricacies of Middle East politics and diplomacy, but they have also taught them about the complexities of joint decision-making and the role of stress in those decisions, the inter-relatedness of events and the problems associated with running an international conference.
The overwhelming impression from the questionnaires is one of enthusiasm for this method of learning, despite the effort involved. As Jaques (1992) suggests, when explaining how simulation-based learning is able to engage the participants so effectively, "the magic ingredient is undoubtedly the imagination, triggered by a sense of play, that activity so often written off because of its association with fun and the supposedly childish connotations that holds".
This paper gives a broad outline of the Middle East Politics simulations from an educational and technological perspective. Internet-based simulations are very much in the interests of the university, as they can expand international links, provide an engaging application for the new technology of the Information Superhighway, and are a good demonstration of innovation in quality education.
The links provide access to a collection of information about an example simulation.
| Time | Lecturers | Students | Controllers | WebMaster | Programmers |
|---|---|---|---|---|---|
| Week 1 | Determine roles; partition roles between classes; select controllers | Form teams and choose roles | |||
| Week 2 | Design scenario | Prepare role profiles | Install role profiles on the Web | Create computer accounts, one per role; set up mail aliases and account/role mapping | |
| Week 3 | Conduct training sessions | Attend training sessions; obtain accounts; practice using computer system | Assist at training sessions; meet students | Ensure that help, guideline Web pages installed | Conduct training sessions |
| Week 4 | Release scenario | Play simulation; prepare for teleconference | Monitor simulation messages | Maintain Web pages for media roles | Monitor system to ensure no problems |
| Week 5 | Monitor simulation | Play simulation; prepare for teleconference | Monitor simulation messages | Maintain Web pages for media roles | Fix any system problems |
| Week 6 | Monitor simulation | Play simulation; prepare for teleconference | Monitor simulation messages | Maintain Web pages for media roles; place teleconference agenda on Web | Fix any system problems |
| Week 7 | Attend teleconference; assess messages for grading | Participate in teleconference; complete questionnaire write de-briefing report | Attend teleconference; assess messages for grading | Assist in setting up computer links for teleconference | |
| Week 8 | Finalise grading | Close computer accounts |